What are Cyber Frameworks and How Should You Choose the Right One?
- IT Risk & Cyber Risk
- 22 December 22

Introduction
Cyber risk and resilience are among the top concerns for businesses today. An organization’s cyber defense infrastructure is only as strong as its weakest link. The fast-evolving cyber risk landscape is keeping CISOs and security teams on their toes. It is imperative to adopt the right cyber framework and establish strong controls to actively manage cyber risks and build cyber resilience. But, where to start?
To help you better understand cyber frameworks, controls, and making the right choice, we present a two-part blog series:
- Understanding IT/cyber frameworks and how they are used to manage IT and cyber risks
- Understanding IT/cyber controls, choosing them effectively, and harmonizing them across frameworks.
What are Cyber Frameworks?
Using and adapting a term borrowed from the construction industry, a cyber framework can be loosely defined as a system of standards, guidelines, and best practices to manage risks that arise in the digital world. The intent is to give IT/cyber risk and security managers a reliable, systematic way to identify, prioritize, and mitigate cyber risk no matter how complex the environment might be. A framework also provides the guide rails and the boundaries of any program so that desired objectives are met without taking on activities out of scope.
Frank Kim, Ex-CISO, SANS Institute, has intelligently classified the multitude of cybersecurity frameworks into these 3 categories, of which cyber risk management forms one dedicated category:
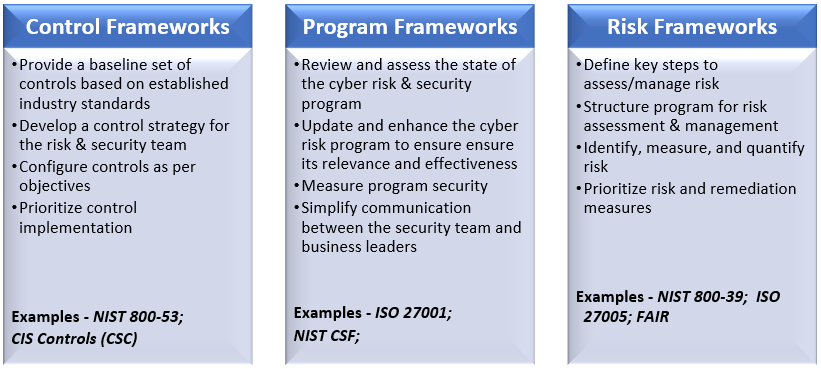
Some frameworks may completely fit into one of the above categories, while others may have overlaps between the three categories.
Frameworks can also be classified by their applicability, as follows:
Mandatory – These frameworks must be compulsorily implemented and complied with depending on the region or sector of operations. They are split further into:
- a. Regulatory: These are mandated by local laws/regulations
- b. Industry-Specific: These are mandated by regulators or service receivers
Examples
GDPR mandated for all companies operating in the EU region,
SAMA mandated for all companies operating in the Republic of Saudi Arabia,
HIPAA mandated for all healthcare providers in the US.- Optional – These are frameworks that are provided as guidelines but are not necessarily mandatory to implement or comply with.
Examples
ISO 27001, CIS, FAIR
Choosing Frameworks
With the plethora of frameworks available, it can get confusing to choose the appropriate ones. Even for seasoned cyber risk management professionals, this issue can cause confusion. The best way to start is by determining these three aspects first:
- Which regions are operations carried out in?
- Which industry(ies) is the business involved in?
- What is the current maturity level of the cyber risk management program?
This will help determine a baseline framework to implement. After this, specifics such as business objectives & goals, potential threats & vulnerabilities, existing policies and treatment procedures, and budget resources should be considered to determine additional framework requirements. The infographic released by NIST provides a good place to start.
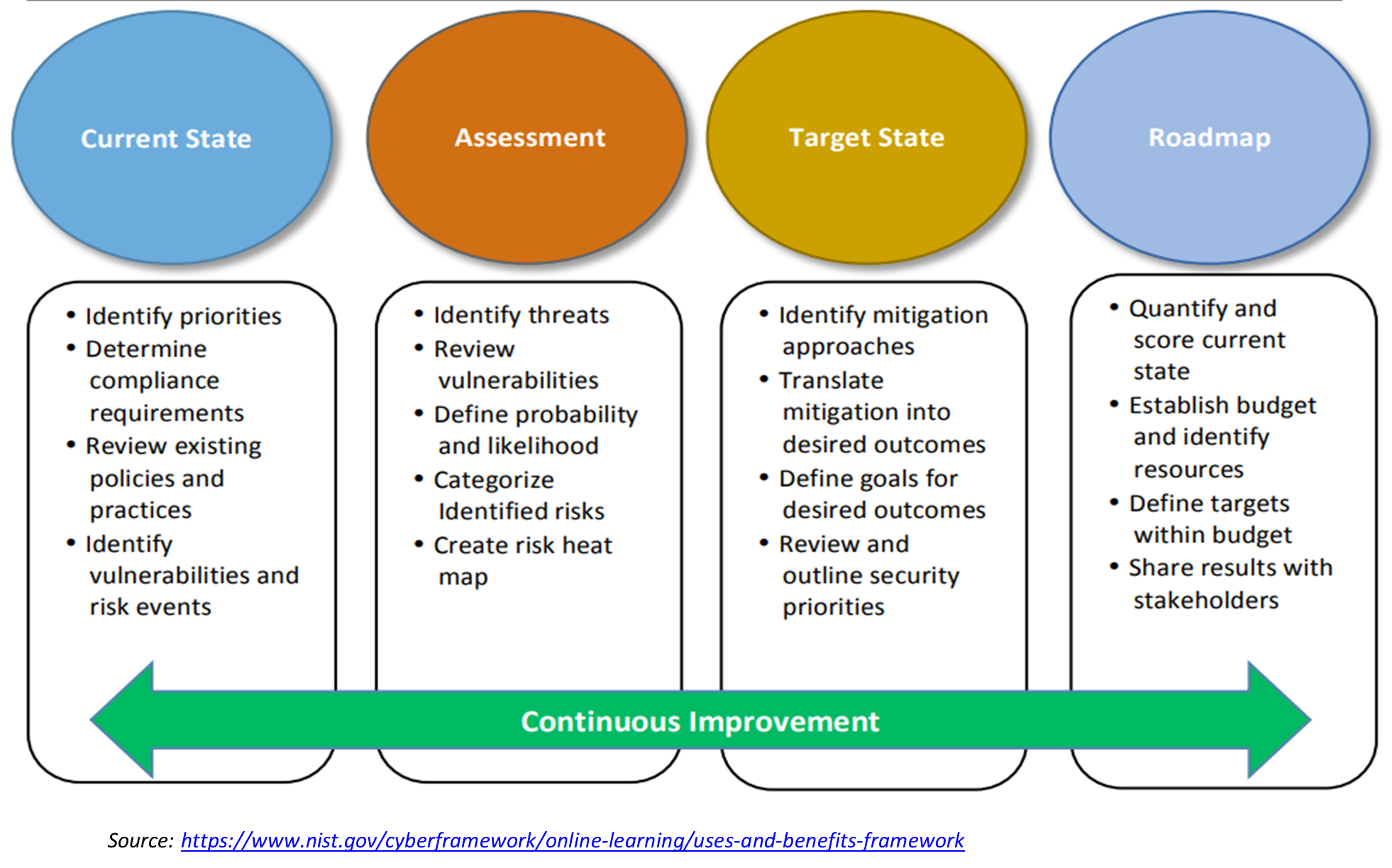
It is always advisable to start simple with the most basic of the applicable frameworks and ensure that the frameworks are aligned with business goals & objectives. And it is imperative to continuously assess and review the success of implemented frameworks. Once there are mature processes in place, the organization may consider gradually scaling up in sophistication and complexity.
To learn more about cyber frameworks, click here. Watch this space for the second part of the series, “What are Controls and How to Achieve Control Harmonization?”.








