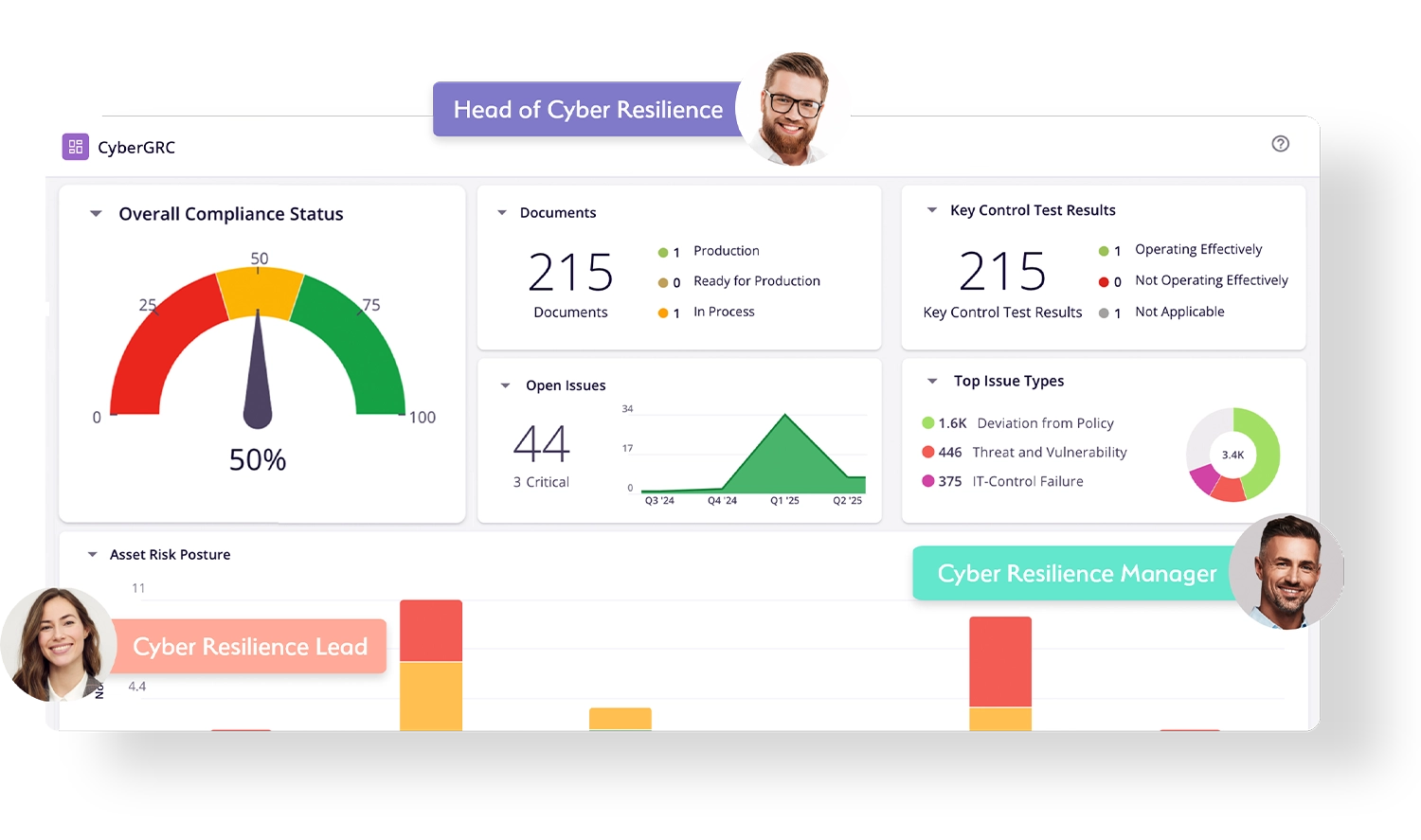
Measure Your Program Outcomes
Source: Based MetricStream customer responses and GRC Journey Business Value Calculator
-
 66 %
66 %reduction in the time taken to complete risk assessments
-
 37 %
37 %cost savings in risk assessment and related processes
-
 50 %
50 %time savings in tracking and linking policies to regulations
Automate and Enhance Cyber Governance, Risk, and Compliance (GRC) Processes
MetricStream Cyber GRC helps organizations actively manage cyber risk through an IT and Cyber Risk and Compliance Framework that aligns with established security standards so you can pass IT audits more efficiently and get buy-in from top management. Gain comprehensive visibility into the overall IT risk posture and cybersecurity investment priorities. Get your IT and Cyber Compliance program up and running quickly with pre-packaged content and industry frameworks such as ISO 27001, NIST CSF, and NIST SP800-53, and map policies to IT controls and policy exceptions. Leverage best practices, insightful reporting, and risk quantification.
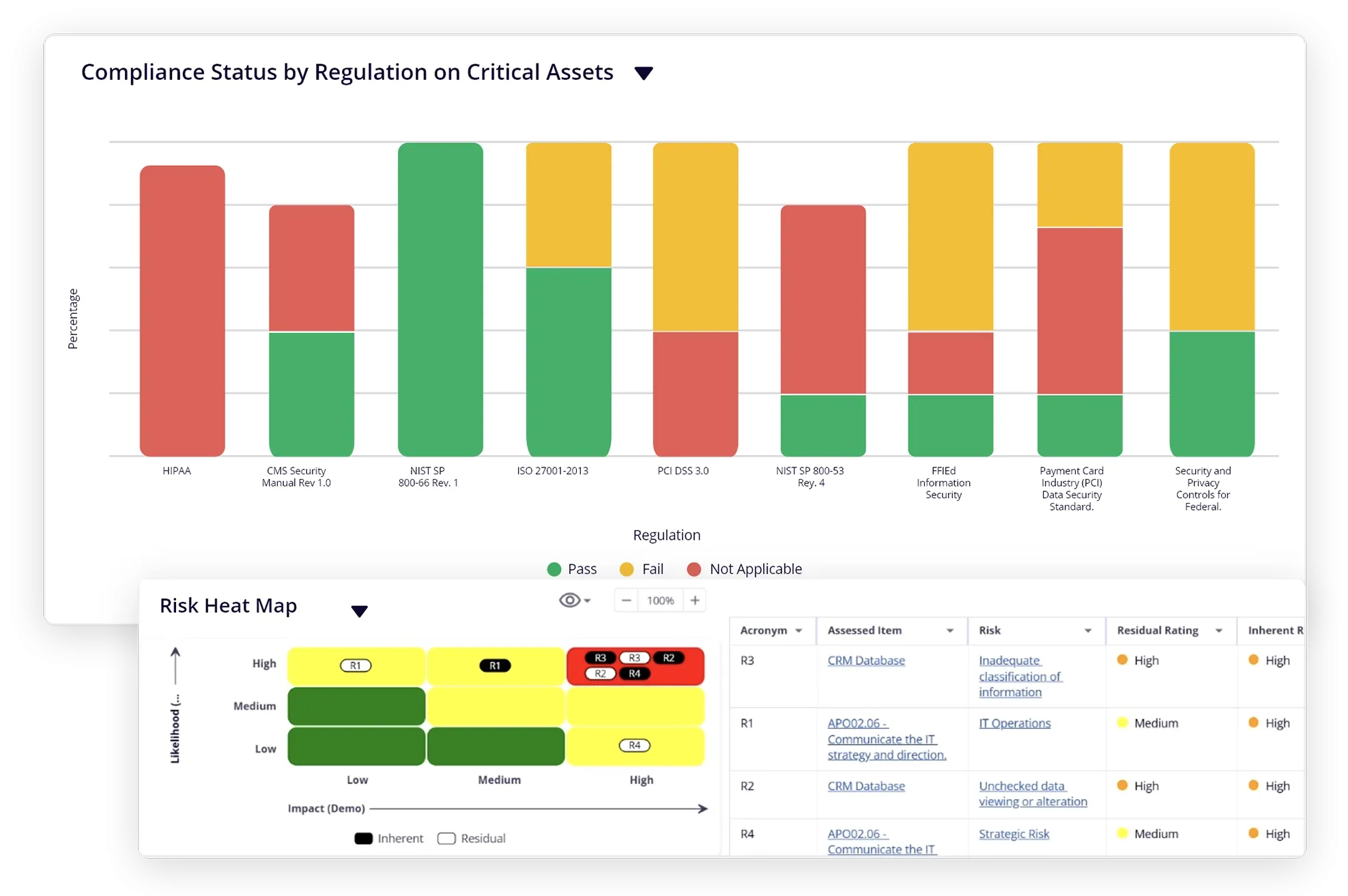

How Our Cyber GRC Helps You
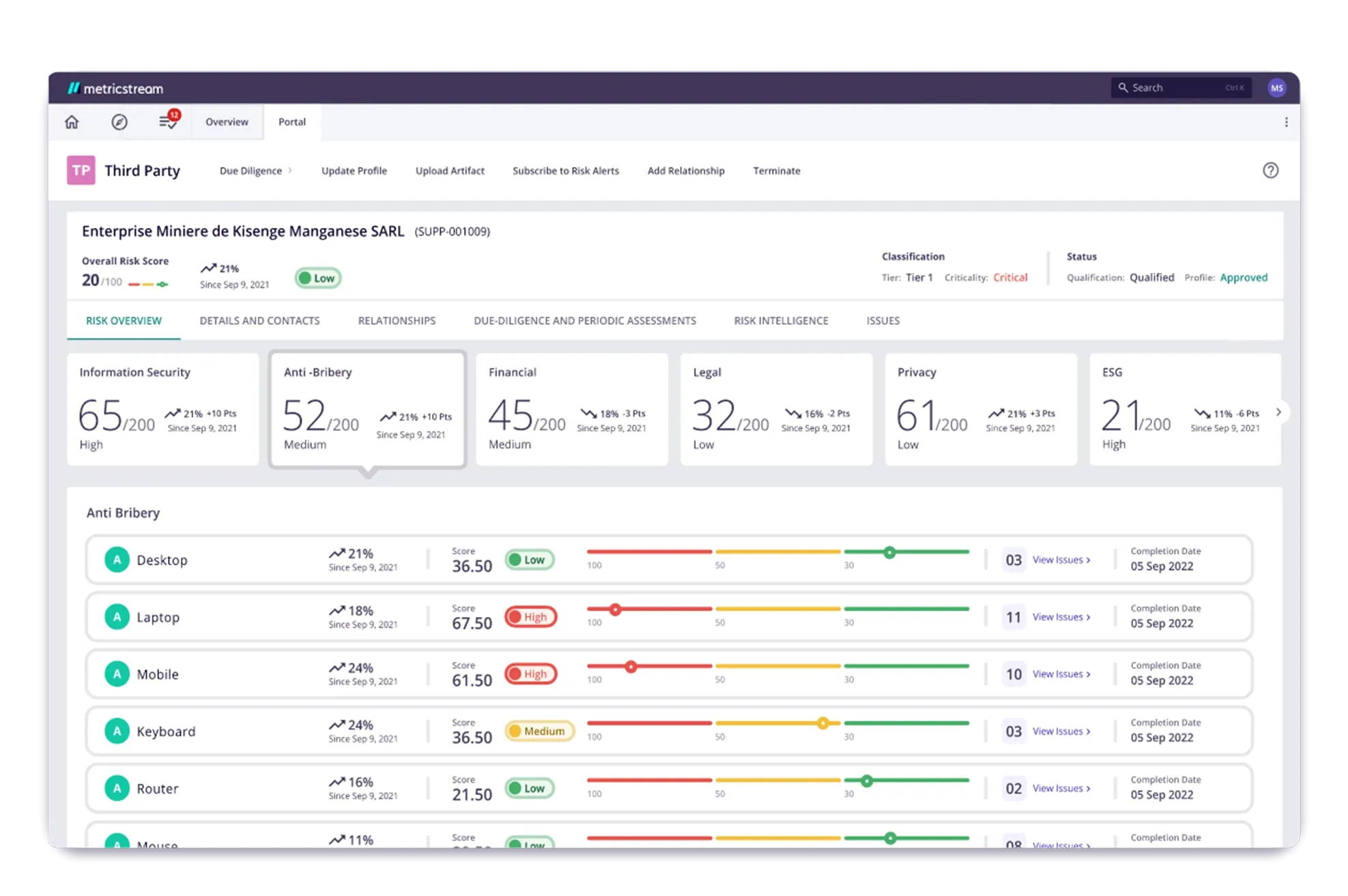
Adopt a streamlined, proactive, and business-driven approach to IT and cyber risk management and mitigation. Define and maintain data on IT and cyber risks, assets, processes, and controls. Assess, quantify, monitor, and manage IT and cyber risks using industry-standard IT risk assessment frameworks, such as NIST, ISO, and more. Manage issues through a closed-loop process of issue investigation, action planning, and remediation.
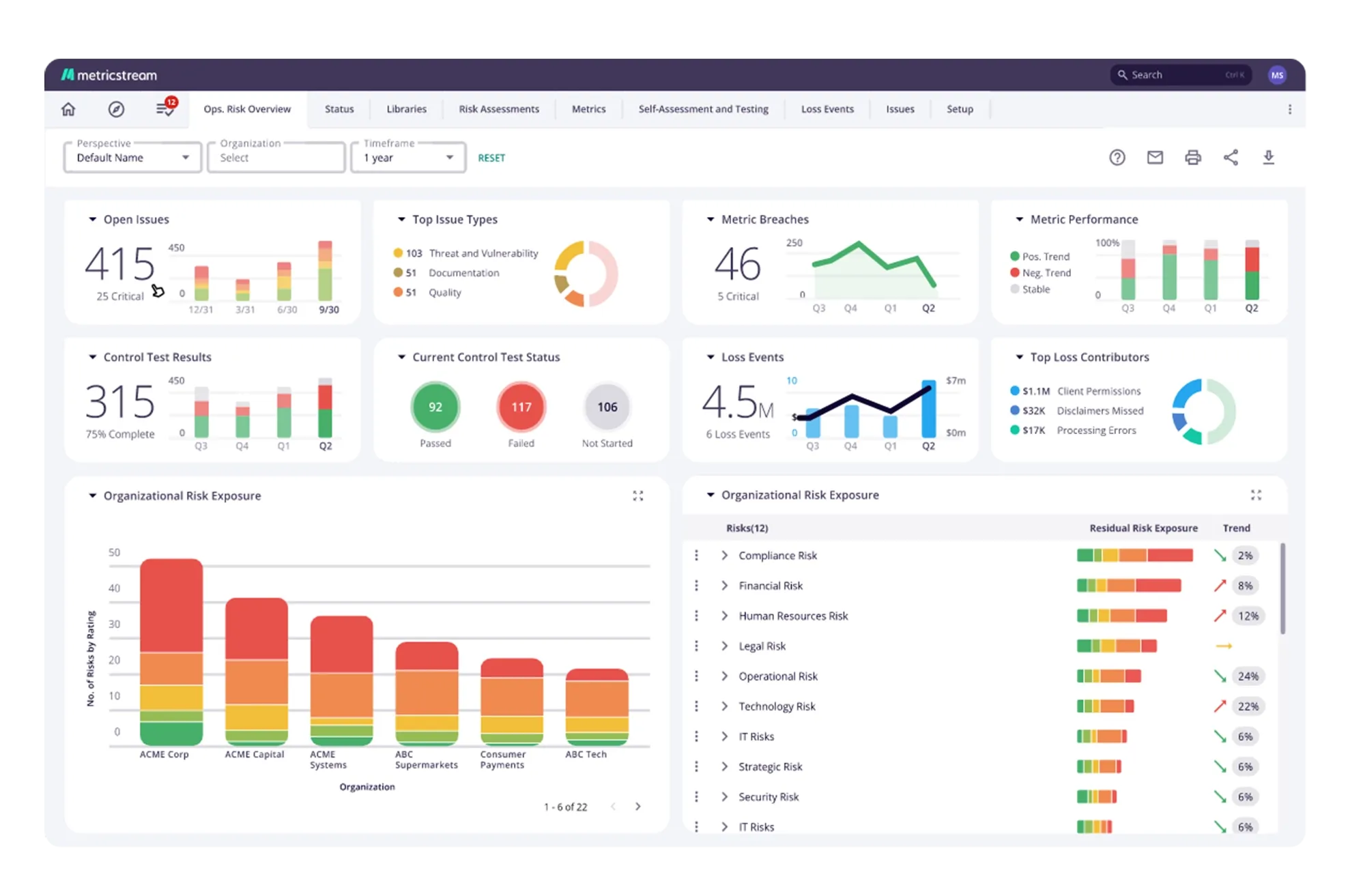
Manage and monitor IT and cyber compliance processes based on various security frameworks and standards. Create and maintain a central structure of the overall IT and cyber compliance hierarchy. Link IT and cyber compliance controls and assessment activities based on your organization’s specific security requirements. Structure and streamline the processes for documenting, investigating, and resolving IT compliance and control issues.
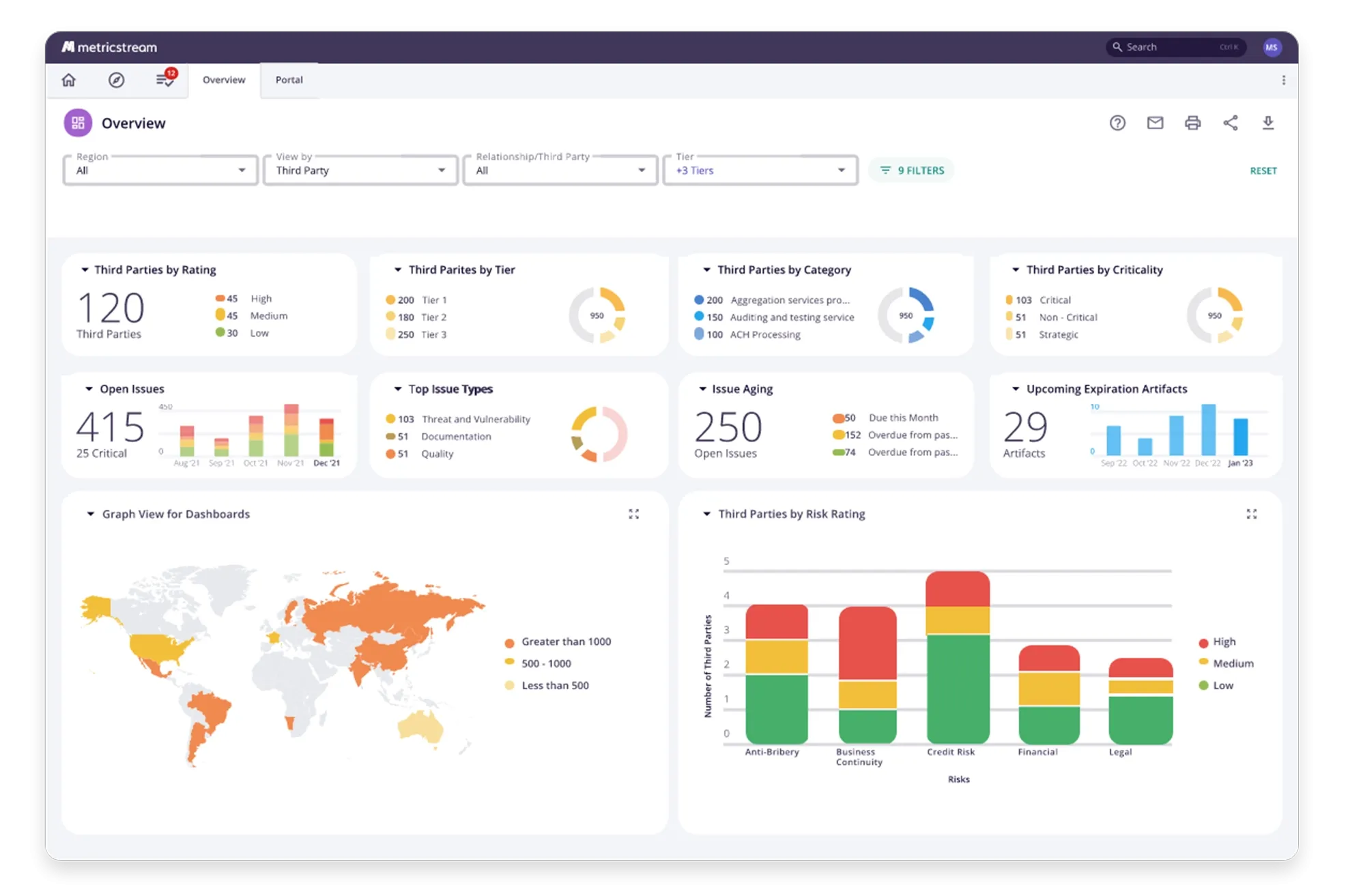
Enable a systematic approach to IT policy management across business units, divisions, and global locations. Easily create policies – either by entering the required information into the system or by uploading an existing policy as an attachment. Strengthen IT compliance by linking IT and cyber policies to asset classes, requirements, risks, controls, processes, and organizations. Trigger policy review and revision cycles through automated notifications and task assignments.
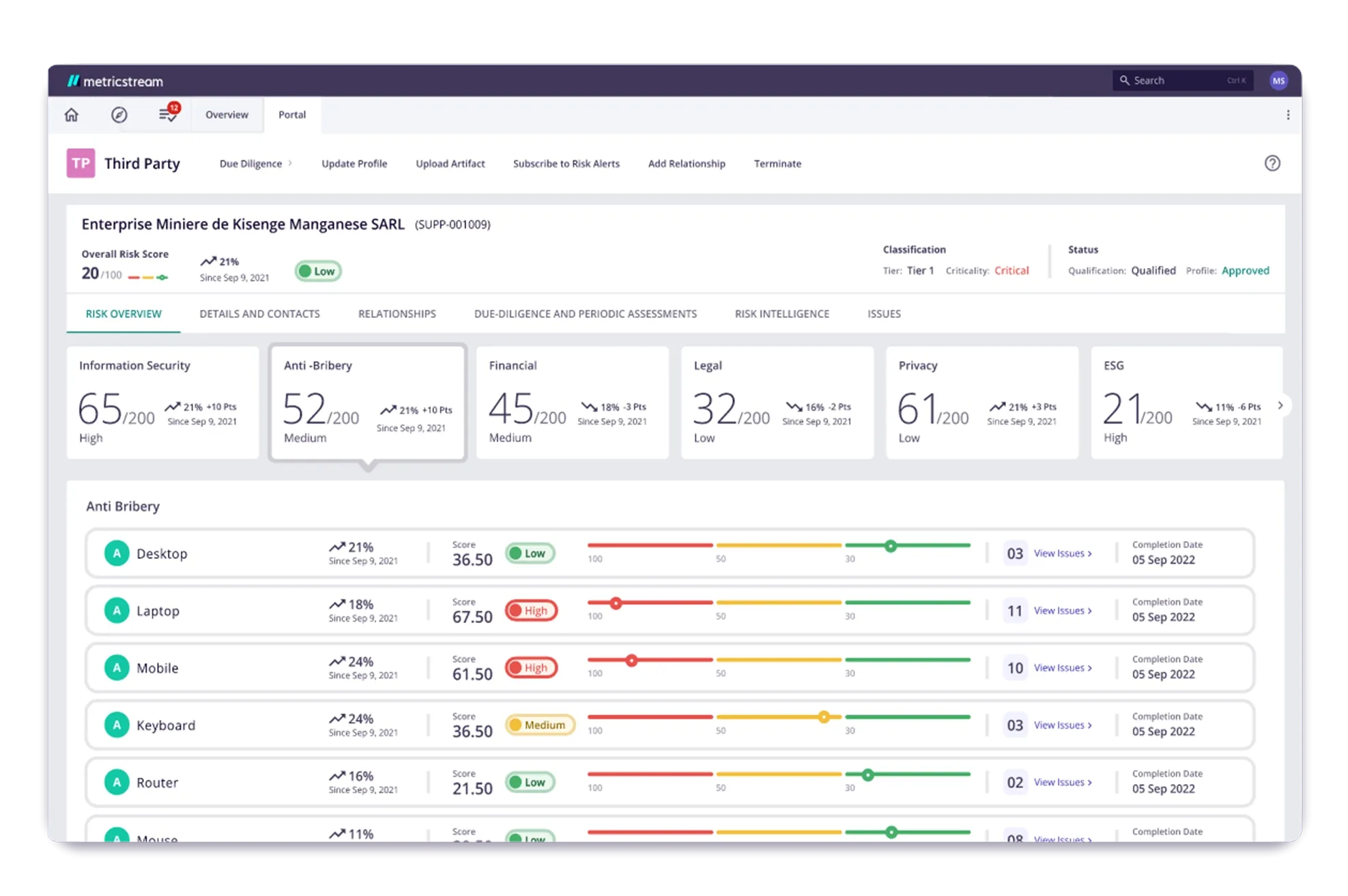
Identify, assess, mitigate, and monitor IT vendor risks while also managing vendor compliance. Leverage automated workflows to accelerate registration and onboarding processes of IT vendors, conduct risk assessments, continuous vendor monitoring, and risk mitigation. Simplify due diligence by leveraging pre-defined questionnaires to assess vendor risks. Leverage powerful reports and analytics to gain deeper insights into vendor risks, compliance, and performance.
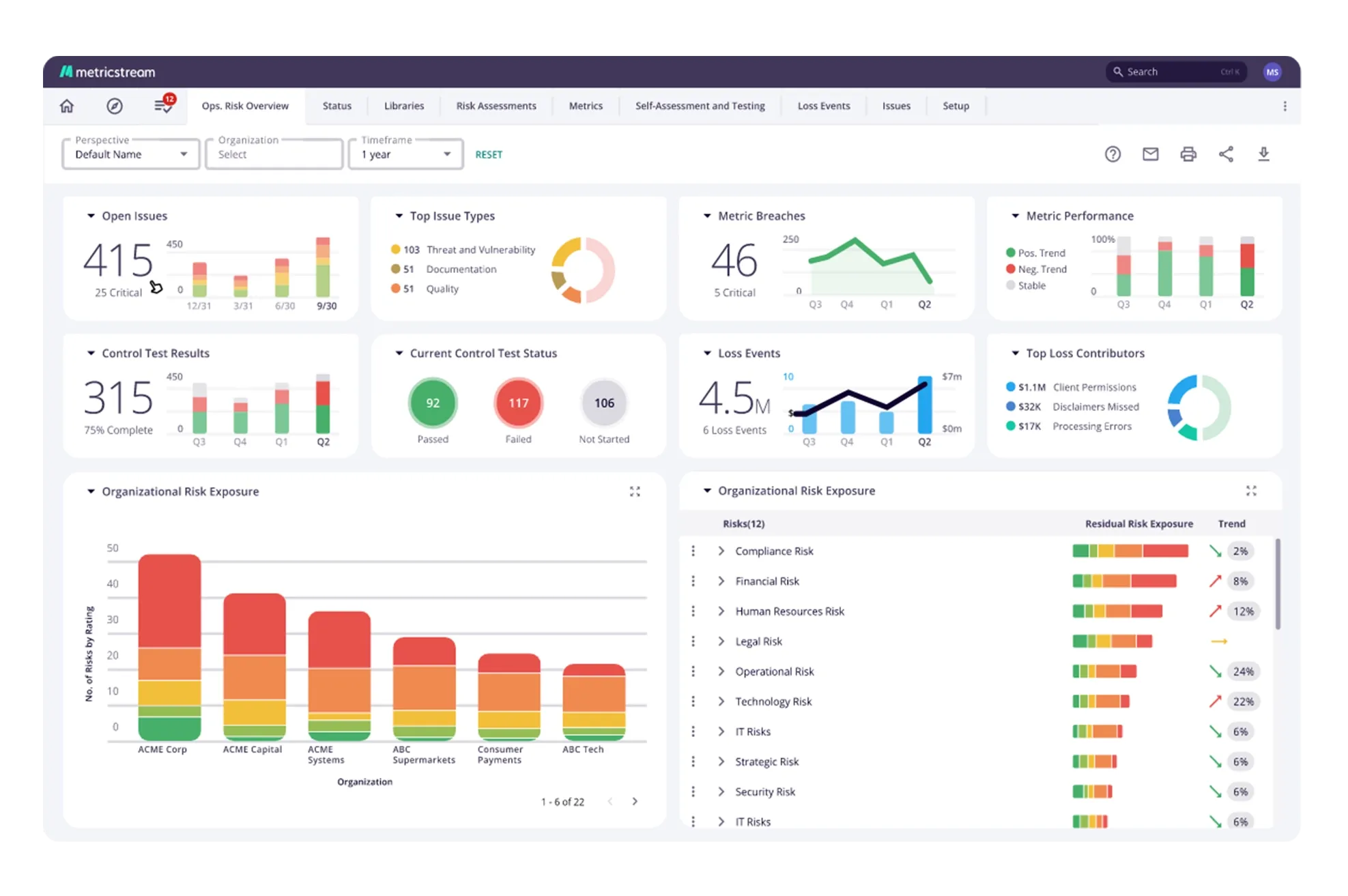
Express your cyber risk exposure in monetary terms to analyze and communicate risk. With support from the FAIR model, accurately determine the monetary impact of cyber risks like data breaches, identity theft, infrastructure downtime, etc. Leverage simulation techniques for transforming range-based estimates into more accurate values. Enable executives to better prioritize cyber investments and drive alignment between cyber programs and the overarching risk management strategy.
How Our Cyber GRC Benefits Your Business
- Build confidence with leadership and regulators through robust enterprise-wide cyber risk management. Gain real-time visibility into threats and vendor risks, improve efficiency by prioritizing remediation, and quantify cyber risks in business terms for proactive communication and mitigation.

Frequently Asked Questions
The GRC (Governance, Risk, and Compliance) approach to managing cybersecurity brings structure, strategy, and accountability to an area often marked by complexity and urgency. Instead of treating cybersecurity as a siloed IT concern, GRC frameworks integrate it into the broader organizational risk landscape. This means aligning cybersecurity efforts with business objectives, assessing cyber risks in context, and ensuring compliance with regulatory mandates - all while creating clear governance structures. A GRC-based approach helps organizations shift from defense to resilience by unifying policies, risk assessments, incident response, and reporting within a centralized, auditable system.
GRC plays an important role in transforming cybersecurity from a purely technical function into a business-enabling discipline. It helps companies identify and prioritize cyber risks, establish clear accountability through governance policies, and ensure that controls meet both regulatory and internal standards. With GRC, cybersecurity is no longer just about patching vulnerabilities, it’s about understanding how those very vulnerabilities affect your strategic objectives and reputation. By bringing visibility, coordination, and rigor to cybersecurity efforts, GRC empowers decision-makers to allocate resources much more effectively, respond confidently to threats, and stay compliant in a dynamic regulatory environment.
In the context of cybersecurity, GRC refers to the integrated processes and tools that help organizations govern their security practices, assess and manage cyber risk, and stay compliant with relevant regulations and standards. A cyber GRC solution typically includes capabilities like risk assessments, control management, incident response workflows, policy enforcement, and compliance tracking - all within a unified platform. It acts as a bridge between technical security operations and enterprise governance, ensuring that cybersecurity decisions are informed by risk intelligence and aligned with business objectives.