Measure Your Program Outcomes
Source: Based on MetricStream customer responses and GRC Journey Business Value Calculator

0
reduction in the time taken to complete risk assessments

0
cost savings in risk assessment and related processes

0
time savings in tracking and linking policies to regulations
Protect Your Digital Enterprise by Reinforcing Cyber Governance
The MetricStream Cybersecurity Risk Management software solution is a part of the CyberGRC solution which enables organizations to stay ahead by proactively anticipating and mitigating IT and cyber risks, threats, vulnerabilities, and multiple IT compliance requirements. The solution helps streamline cybersecurity efforts to achieve cyber resilience. Built on the MetricStream Platform, the solution cuts across enterprise siloes, aggregating information and providing a 360-degree, real-time view of IT risk, compliance, policy management, and IT vendor posture. The solution also enables enterprises to execute and manage an effective business continuity and disaster recovery program.
READ MORE Product Description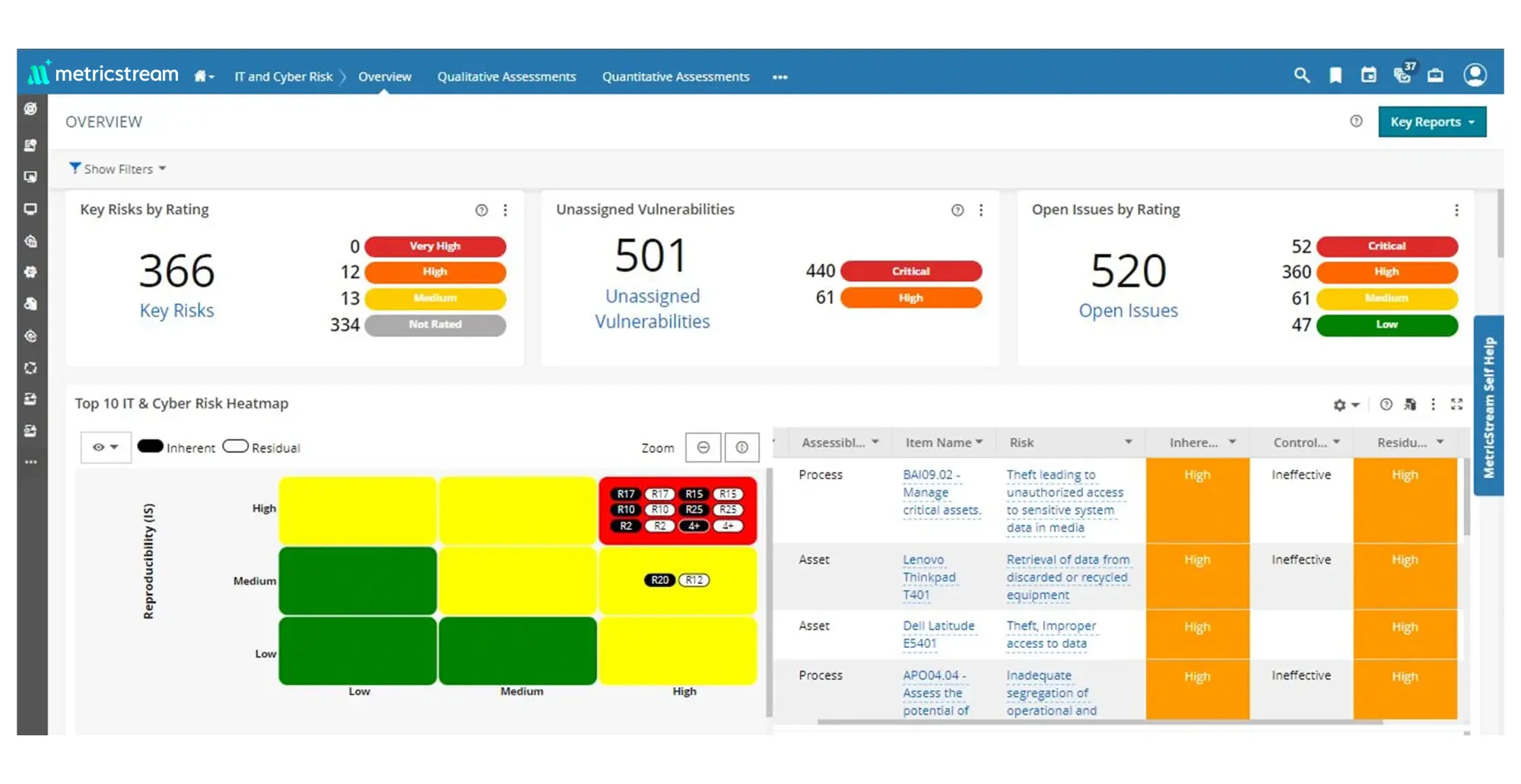
How Our Cybersecurity Risk Management Software Solution Helps You
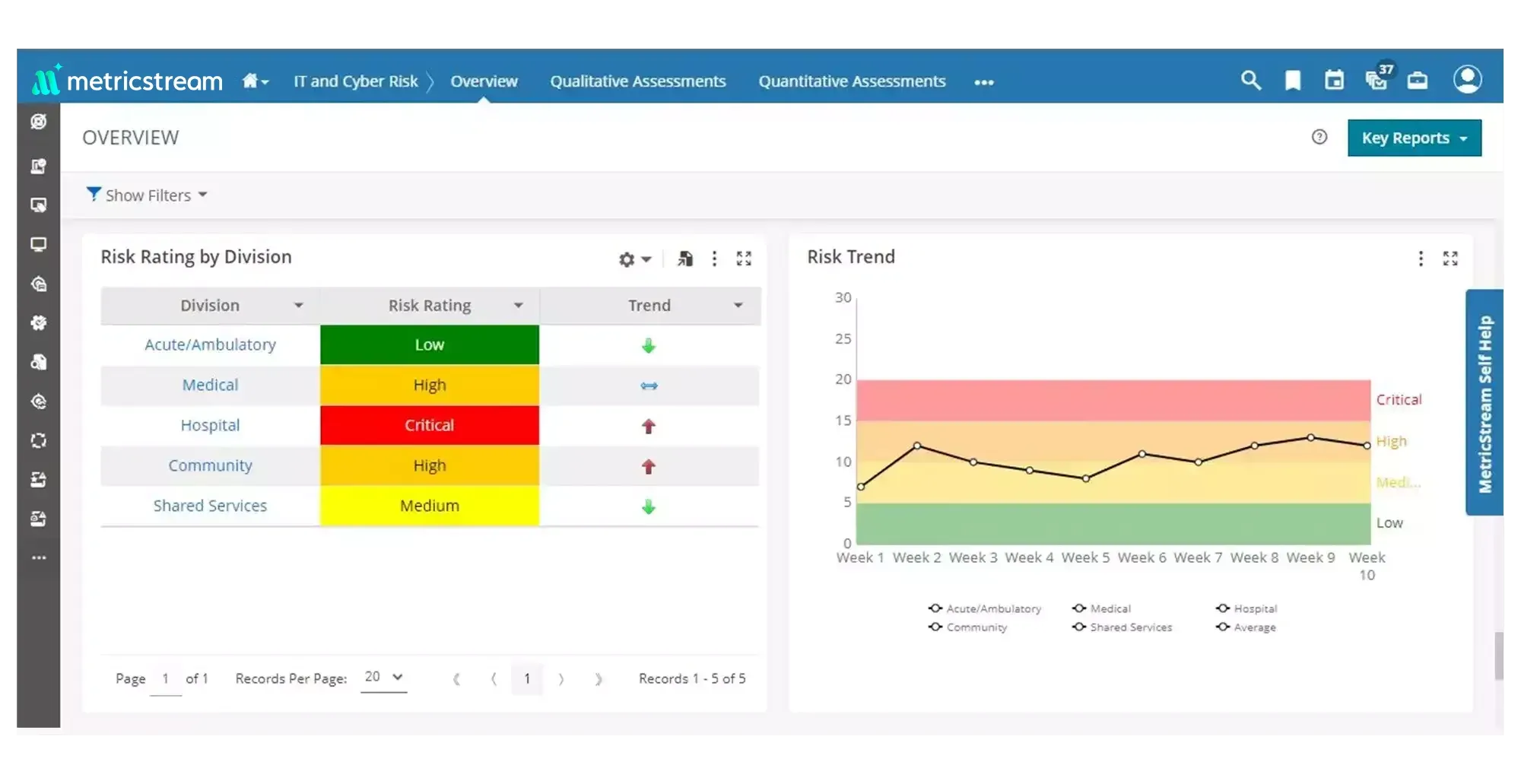

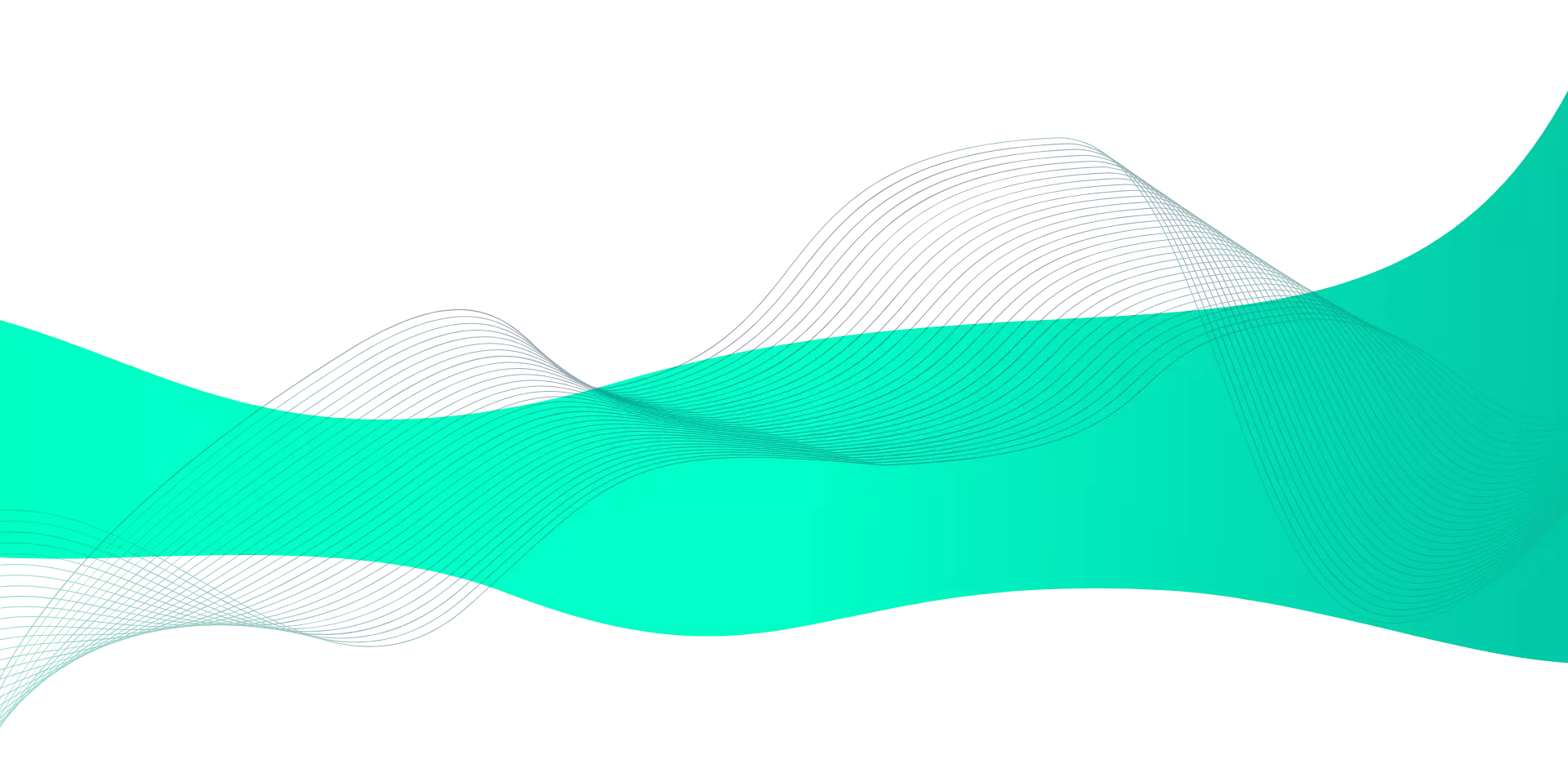
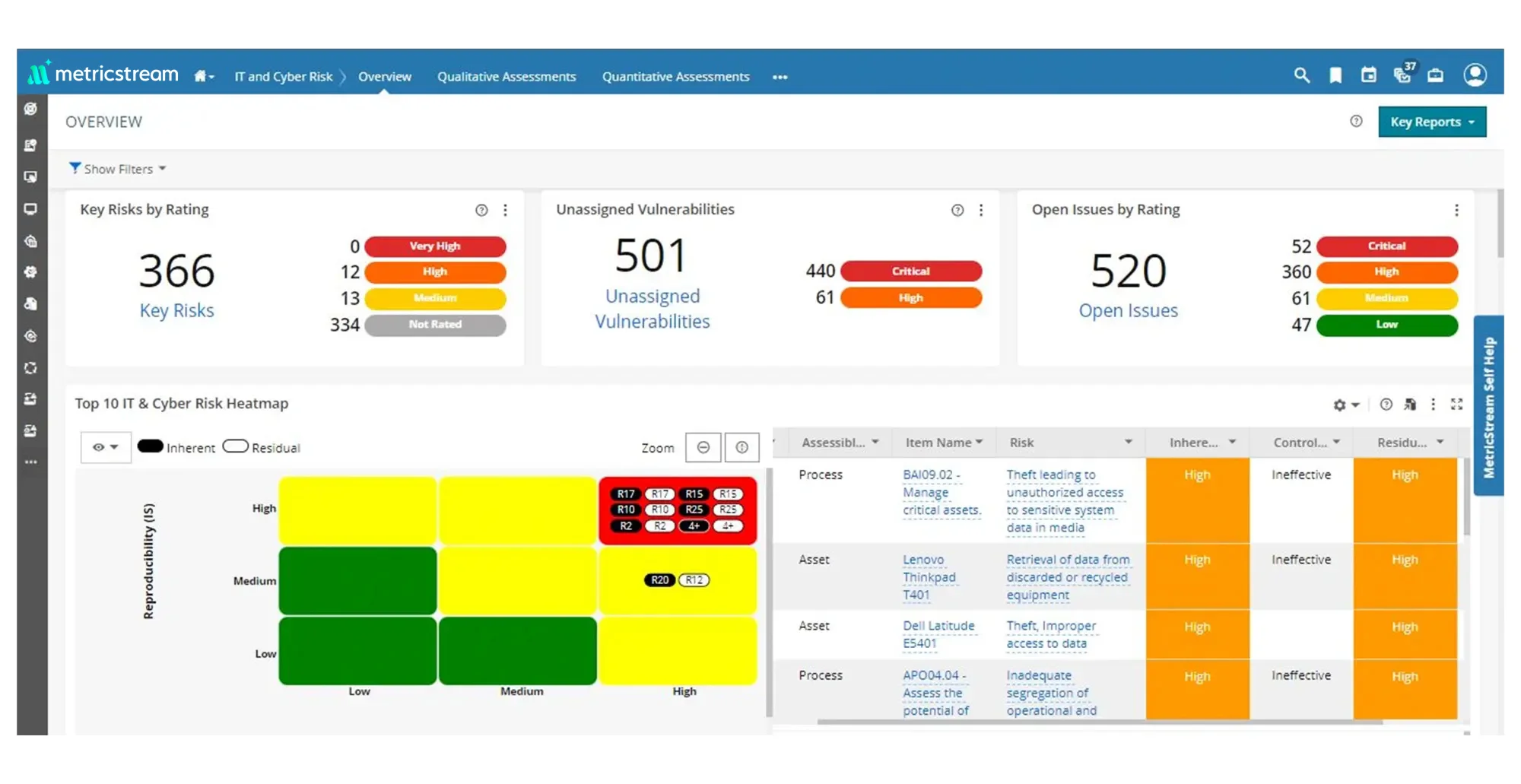
Comprehensive Visibility into Cybersecurity Risks
Define and maintain data on cybersecurity risks, assets, processes, and controls in a centralized repository. Assess, quantify, monitor, and manage cybersecurity risks using industry standards and risk assessment frameworks. Enhance visibility and gain contextual risk insights by mapping IT assets to cybersecurity risks, IT vendor risks, threats, and vulnerabilities and associated details such as description, category, hierarchy, ownership, and validity.
Consolidated Threat and Vulnerability Intelligence
Import, aggregate, prioritize, track, and remediate cybersecurity threats and vulnerabilities in an efficient, collaborative manner. Drive better-informed decisions on vulnerability remediation strategies by determining combined risk ratings for business assets based on the vulnerability severity and the asset criticality rating.
Robust Cybersecurity Compliance with Effective IT Controls
Manage and monitor compliance with a range of IT regulations and standards in an integrated manner. Maintain a centralized repository for all associated processes, assets, risks, controls, and audits. Harmonize control sets across multiple regulatory requirements to eliminate duplication of controls. Assess and manage IT controls in an integrated manner using industry standard frameworks such as ISO 27001 and NIST.
Continuous Control Testing and Monitoring
Set up autonomous processes for the continuous testing and monitoring of your cloud security controls. Adopt a proactive approach to identifying vulnerabilities and control weaknesses to strengthen cloud security. Strengthen compliance posture by mapping cloud security controls with your internal controls that are aligned to compliance standards, such as HIPAA, NIST CSF, PCI, and ISO 27001.
Cyber Risk Quantification
Quantify cybersecurity risk in business and monetary terms, enabling proactive communication and management of risk exposure. Drive better-informed cybersecurity investment decisions with support from the FAIRTM model. Improve accuracy in determining the monetary impact of cybersecurity risks such as data breaches, identity theft, infrastructure down time, etc.
Efficient Business Continuity Planning
Easily maintain and carry out business continuity plans from templates and map them to associated business processes and functions, critical resources, IT assets, key contacts, and locations. Regularly assess the business continuity plans to check if the outlined activities are relevant and effective.
AI-Powered Intelligent Issue Management
Identify and document issues from cybersecurity risk and compliance assessments through a closed-loop process of issue investigation, root cause analysis, and remediation. Leverage AI-powered capabilities to identify issues based on relation and recommend issue classification in a quick and efficient manner.
How Our Cybersecurity Risk Management Software Solution Benefits Your Business
- Build confidence with executive management, regulators, and other stakeholders by adopting an enterprise-level approach to cybersecurity risk management and resilience
- Gain real-time visibility into cybersecurity risks and threat exposure through quantified and contextual risk information from across processes and assets
- Optimize efficiency by correlating cyber vulnerabilities with IT assets and prioritizing remediation measures based on criticality
- Drive better-informed cybersecurity investment decisions and improve communication of cyber risk exposure to the top management and the board