Introduction
Cloud computing is no longer a novelty – it’s a fixture in corporate IT. Much of the cloud’s appeal can be attributed to its flexible computing power, high availability, and low capital costs. And, though it’s a shared resource, cloud security has been a major priority, putting early fears of “the cloud isn’t safe” to rest.
Still, bad actors continue to find newer and better ways of attacking the cloud to steal sensitive data. All it takes is a vulnerability in one of your cloud applications for attackers to slip inside your network, undetected. According to the 2022 Thales Cloud Security study, 45% of surveyed organizations said that they have experienced a data breach or failed an audit involving data in the cloud.
Many organizations assume that their cloud service providers (CSPs) will handle all their security needs. This is only partially true. While CSPs do safeguard certain cloud components, you’re ultimately responsible for the security of everything else, including your data and endpoints.
If you’ve already implemented effective cloud security controls, great! But that’s only half the job. You also need to verify if your controls are working as intended and in line with industry best practices. Continuous Control Monitoring (CCM) helps you proactively identify control gaps and areas of improvement that can be tackled before a serious security issue occurs.
The best part is that CCM by nature is automated and always on – so you don’t have to waste your time and resources manually monitoring controls. Technology does the heavy lifting, enabling you to focus on the more impactful and strategic aspects of cloud security.
In this eBook, we explore why CCM is essential to improving your cloud security risk and compliance posture, and, ultimately your IT and cyber risk management processes. We also look at how MetricStream CCM makes control monitoring across compliance frameworks and requirements – like NIST-CSF, PCI-DSS, SOC 2, and HIPAA – quick, simple, and autonomous.
As a result, you’re able to build a stronger, more secure cloud environment, reducing your risk, improving compliance, and controlling your costs – while protecting your organization from serious business and reputational impact.
CCM in the Cloud – A Business Imperative
Your data, IT assets, and applications in the cloud are not risk-free. To protect your organization from threats and vulnerabilities, such as malicious attacks, insecure APIs, third-party vulnerabilities, misconfigurations, and more, there are a number of cloud security controls, often running into hundreds. These include access controls, password policies, key management, data encryption, two-factor authentication, and automating data backups, among others.
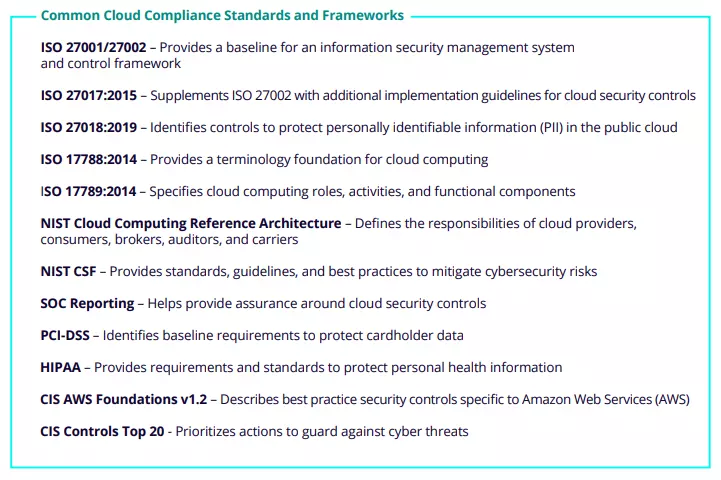
Cloud security controls aren’t just essential for threat mitigation, but also for compliance. There are a multitude of standards, frameworks, and regulations that companies in the cloud are expected to adhere to.
These cloud security controls need to be tested and monitored to ensure they are working as intended. Manually testing every cloud security control or relying on electronic document management and generic desktop tools not only takes time but is also resource-intensive, error-prone, expensive, and ineffective, especially given today’s fast-paced environment.
CCM continuously monitors control effectiveness and automatically gathers the evidence needed to show compliance. This iterative, autonomous testing process enables you to proactively detect and mitigate anomalies that could otherwise go unnoticed. It provides a true picture of your organization’s cloud security and compliance posture.
Compared to traditional manual, sample-based control monitoring, CCM offers wider coverage with complete testing, faster results, and better accuracy. It also helps reduce the time and audit costs with constant evidence collection. And since the process is automated, it frees you up to concentrate on riskier areas, issue remediation, and other impactful actions to strengthen cloud security.
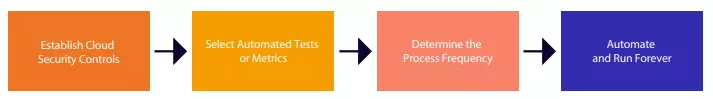
Set Up Once, Monitor Continuously
Here are the key steps involved in getting CCM started:
- Establish Cloud Security Controls
First, organizations need to set up cloud security controls intended to mitigate various risks and in line with the applicable industry frameworks and regulations issued by oversight bodies, such as HIPAA (for healthcare), PCI-DSS (for the payments industry), and NIST CSF. Map cloud security controls to the corresponding risks, assets, regulations, testing processes, and policies on a many-to-many basis in a centralized repository. - Select Automated Tests or Metrics
Next, specify and embed automated tests or metrics that will help verify whether the cloud security controls are effective and working as intended. - Determine the Process Frequency
Lastly, organizations need to determine the process frequency to perform cloud security control tests – either continuously or at selected intervals. Continuous, or close to it, is recommended. - Once the continuous control monitoring process is all set and running in the cloud, organizations can be rest assured that all their cloud security controls are being continuously monitored. They will be able to effectively reduce risks with continuous testing of controls, automatic evidence collections, and automated notifications to control owners for the identified exceptions or deviations.
5 Reasons Why CCM In the Cloud Is Critical
In today’s era of rising cloud security threats, compliance requirements, and demands to do more with less, CCM can help you achieve the following benefits:
- Enhanced Cloud Security and Compliance: No more worrying about security gaps in the cloud. CCM provides continuous updates on whether your controls are configured correctly, aligned with compliance requirements, and performing as expected. Autonomous processes help ensure that control failures aren’t missed due to human error. Improve stakeholder confidence in your cloud security posture and assurance reports.
- Optimized Operational Efficiency: CCM, along with automated evidence collection, helps you test more cloud controls in less time. Quickly detect anomalies before they snowball into serious issues – all with minimal human effort. Security teams, freed from tedious control testing, have more time to focus on proactively mitigating threats and vulnerabilities, instead of reacting to them.
- Reduced Security Costs: By identifying control weaknesses before they escalate, you can lower the costs of remediation. With faster, complete, continuous control monitoring and automated evidence collection, audit teams will save considerable time and resources otherwise spent on in-depth control testing.
- Improved Decision-Making: CCM provides CISOs and other executives with a unified, real-time view of the control environment, highlighting control gaps and weaknesses. This helps leadership make faster, better decisions on where to improve cloud security.
- Better Agility and Adaptability: With CCM, you always have complete visibility into your control environment. So, if a cloud application or network is at risk, you can implement mitigation measures right away, staying a step ahead of security risks. CCM gives you the agility and adaptability you need to succeed in a rapidly evolving cyber risk landscape.
How MetricStream Can Help
MetricStream’s Continuous Control Monitoring (CCM) makes testing and monitoring of cloud security controls in line with compliance standards fast, simple, effective, and automatic. Boost confidence in compliance with a proactive, automated, and complete testing approach compared to manual, sample-based testing.
MetricStream CCM enables you to proactively identify vulnerabilities, improve your cyber and cloud security and compliance posture, and reduce audit costs.
Benefits :
- Stay agile, alert, and secure with CCM that is always on and autonomous
- Automatically validate whether your cloud environment (such as AWS) is compliant with the required cyber standards and frameworks
- Improve testing accuracy by moving away from sample-based assessments
- Autonomously gather evidence of control pass/failure, enable users to remediate and resolve issues faster, improve compliance, and reduce audit costs
- Focus on your most critical controls and risks, directing resources towards mitigating risk where it matters most
- Gain comprehensive coverage and visibility into the performance and effectiveness of controls
Combined with MetricStream’s complete CyberGRC solution – including IT and Cyber Risk Management, IT and Cyber Compliance Management, built-in content and frameworks, and risk quantification – CCM can help you strengthen your overarching cyber governance, risk, and compliance program.
Cloud computing is no longer a novelty – it’s a fixture in corporate IT. Much of the cloud’s appeal can be attributed to its flexible computing power, high availability, and low capital costs. And, though it’s a shared resource, cloud security has been a major priority, putting early fears of “the cloud isn’t safe” to rest.
Still, bad actors continue to find newer and better ways of attacking the cloud to steal sensitive data. All it takes is a vulnerability in one of your cloud applications for attackers to slip inside your network, undetected. According to the 2022 Thales Cloud Security study, 45% of surveyed organizations said that they have experienced a data breach or failed an audit involving data in the cloud.
Many organizations assume that their cloud service providers (CSPs) will handle all their security needs. This is only partially true. While CSPs do safeguard certain cloud components, you’re ultimately responsible for the security of everything else, including your data and endpoints.
If you’ve already implemented effective cloud security controls, great! But that’s only half the job. You also need to verify if your controls are working as intended and in line with industry best practices. Continuous Control Monitoring (CCM) helps you proactively identify control gaps and areas of improvement that can be tackled before a serious security issue occurs.
The best part is that CCM by nature is automated and always on – so you don’t have to waste your time and resources manually monitoring controls. Technology does the heavy lifting, enabling you to focus on the more impactful and strategic aspects of cloud security.
In this eBook, we explore why CCM is essential to improving your cloud security risk and compliance posture, and, ultimately your IT and cyber risk management processes. We also look at how MetricStream CCM makes control monitoring across compliance frameworks and requirements – like NIST-CSF, PCI-DSS, SOC 2, and HIPAA – quick, simple, and autonomous.
As a result, you’re able to build a stronger, more secure cloud environment, reducing your risk, improving compliance, and controlling your costs – while protecting your organization from serious business and reputational impact.
Your data, IT assets, and applications in the cloud are not risk-free. To protect your organization from threats and vulnerabilities, such as malicious attacks, insecure APIs, third-party vulnerabilities, misconfigurations, and more, there are a number of cloud security controls, often running into hundreds. These include access controls, password policies, key management, data encryption, two-factor authentication, and automating data backups, among others.
Cloud security controls aren’t just essential for threat mitigation, but also for compliance. There are a multitude of standards, frameworks, and regulations that companies in the cloud are expected to adhere to.
These cloud security controls need to be tested and monitored to ensure they are working as intended. Manually testing every cloud security control or relying on electronic document management and generic desktop tools not only takes time but is also resource-intensive, error-prone, expensive, and ineffective, especially given today’s fast-paced environment.
CCM continuously monitors control effectiveness and automatically gathers the evidence needed to show compliance. This iterative, autonomous testing process enables you to proactively detect and mitigate anomalies that could otherwise go unnoticed. It provides a true picture of your organization’s cloud security and compliance posture.
Compared to traditional manual, sample-based control monitoring, CCM offers wider coverage with complete testing, faster results, and better accuracy. It also helps reduce the time and audit costs with constant evidence collection. And since the process is automated, it frees you up to concentrate on riskier areas, issue remediation, and other impactful actions to strengthen cloud security.

Here are the key steps involved in getting CCM started:
- Establish Cloud Security Controls
First, organizations need to set up cloud security controls intended to mitigate various risks and in line with the applicable industry frameworks and regulations issued by oversight bodies, such as HIPAA (for healthcare), PCI-DSS (for the payments industry), and NIST CSF. Map cloud security controls to the corresponding risks, assets, regulations, testing processes, and policies on a many-to-many basis in a centralized repository. - Select Automated Tests or Metrics
Next, specify and embed automated tests or metrics that will help verify whether the cloud security controls are effective and working as intended. - Determine the Process Frequency
Lastly, organizations need to determine the process frequency to perform cloud security control tests – either continuously or at selected intervals. Continuous, or close to it, is recommended. - Once the continuous control monitoring process is all set and running in the cloud, organizations can be rest assured that all their cloud security controls are being continuously monitored. They will be able to effectively reduce risks with continuous testing of controls, automatic evidence collections, and automated notifications to control owners for the identified exceptions or deviations.

In today’s era of rising cloud security threats, compliance requirements, and demands to do more with less, CCM can help you achieve the following benefits:
- Enhanced Cloud Security and Compliance: No more worrying about security gaps in the cloud. CCM provides continuous updates on whether your controls are configured correctly, aligned with compliance requirements, and performing as expected. Autonomous processes help ensure that control failures aren’t missed due to human error. Improve stakeholder confidence in your cloud security posture and assurance reports.
- Optimized Operational Efficiency: CCM, along with automated evidence collection, helps you test more cloud controls in less time. Quickly detect anomalies before they snowball into serious issues – all with minimal human effort. Security teams, freed from tedious control testing, have more time to focus on proactively mitigating threats and vulnerabilities, instead of reacting to them.
- Reduced Security Costs: By identifying control weaknesses before they escalate, you can lower the costs of remediation. With faster, complete, continuous control monitoring and automated evidence collection, audit teams will save considerable time and resources otherwise spent on in-depth control testing.
- Improved Decision-Making: CCM provides CISOs and other executives with a unified, real-time view of the control environment, highlighting control gaps and weaknesses. This helps leadership make faster, better decisions on where to improve cloud security.
- Better Agility and Adaptability: With CCM, you always have complete visibility into your control environment. So, if a cloud application or network is at risk, you can implement mitigation measures right away, staying a step ahead of security risks. CCM gives you the agility and adaptability you need to succeed in a rapidly evolving cyber risk landscape.
MetricStream’s Continuous Control Monitoring (CCM) makes testing and monitoring of cloud security controls in line with compliance standards fast, simple, effective, and automatic. Boost confidence in compliance with a proactive, automated, and complete testing approach compared to manual, sample-based testing.
MetricStream CCM enables you to proactively identify vulnerabilities, improve your cyber and cloud security and compliance posture, and reduce audit costs.
Benefits :
- Stay agile, alert, and secure with CCM that is always on and autonomous
- Automatically validate whether your cloud environment (such as AWS) is compliant with the required cyber standards and frameworks
- Improve testing accuracy by moving away from sample-based assessments
- Autonomously gather evidence of control pass/failure, enable users to remediate and resolve issues faster, improve compliance, and reduce audit costs
- Focus on your most critical controls and risks, directing resources towards mitigating risk where it matters most
- Gain comprehensive coverage and visibility into the performance and effectiveness of controls
Combined with MetricStream’s complete CyberGRC solution – including IT and Cyber Risk Management, IT and Cyber Compliance Management, built-in content and frameworks, and risk quantification – CCM can help you strengthen your overarching cyber governance, risk, and compliance program.








